
In the age of Internet we tend to do more and more of our daily things using a computer connected to the world wide web. There are lots of reasons behind taking this device-oriented approach including spending less time achieving same goals (like on-line shopping compared to traditional one or e-learning), combining multiple activities using a single tool (e-mail compared to regular mail), communicating with friends/colleagues/business partners and many more.
The challenges of such a shift arise as well. The fair question is ‘Is it safe to convert your life from analog to digital?’ Potential threats have taken distinct shape over the last 10 years. Some of them could take form of viruses and other malware, some could try to scam us using phishing sites. The purpose of those programs is to gain access to our private info.
Lets say you protected yourself from viruses/phishing attacks and finally can feel safe sharing private files on-line.
Table of Contents
It’s Okay Now, right?
For majority of Internet users we would firmly answer ‘Yes’. As for that remaining part of web-converts, namely big companies, entrepreneurs or even security nerds, there’s more to it than just a phishing attack or a Windows virus. All of your data or chat/e-mail/messaging history is stored on a server of that particular service you use everyday which could be a very big deal for people who want data security. After a couple of incidents of icloud account hacking you can no longer feel safe and start taking cloud security measures.
So What Do I Do?
Well, there’s no denying that achieving security is a hard job which requires a lot of efforts and knowledge which is why we decided to put all the info in one place.
Good Old Transposition Cipher:
Do you like solving riddles? If, yes this option could be even a little fun for you. Take a situation when you need to send a password or other short message. Transposition cipher might help you out. The concept is ridiculously simple. We examine a basic rail fence as an example, it takes a sentence and divides the letters into 2 groups using zig zag pattern as shown below:
Write a sentence for example…
'Today is a great day for transferring files securely'
Lets compress it like this first
'todayisagreatdayfortransferringfilessecurely'
then split the text into 2 groups
each word is highlighted with a separate colour
It’s done! You can now send this message to your recipient and inform them about the pattern used to create a cipher via other means of communication (phone, skype, a live conversation)
There are lots of ciphers like that and you do not have to pay a penny to use them. This method have flaws however, knowing the pattern used to encipher the message the hacker would be able to decipher your message so it is recommended that you create your own pattern rather then use examples you find on the web. This method is simple and works great for messages, passwords or other text files.
You can also try automated Message Encryption Services:
1.) Privatoria – Encypts your message and gives you a code to share with the recipient and decode the file.
2.) Crypto-chat – Works more like a secure chat room rather than a message system. You get a secure channel for chatting and share a password with your friend to enter the room.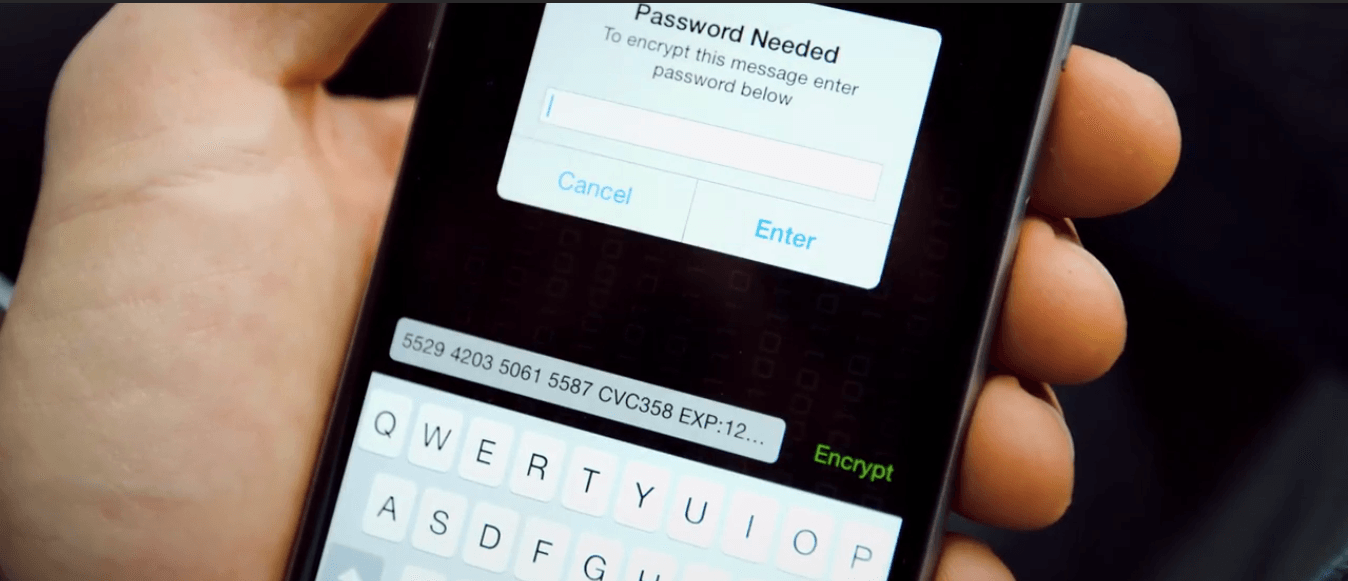
But what do you do when you need to transfer a video file for example. Unfortunately transposition ciphers fall short here therefore you would have to use more complex data encryption methods.
Specialized Services:
Fortunately there’s a good number of on-line services who provide the functionality to transfer files on-line with different storing options. These are some of the high-lights:
Privatoria – Secure file transfer and data storage. Key features are 256 bit AES encryption for the data itself and SSL encryption for the transfer channel. It means the service themselves can’t view the encrypted file as it’s transferred over an encrypted channel. The file is purged from the server after 24 hours or right after the download by the recipient. There’s a 20-digit code to decrypt the file. Share with the recipient via any other channel (phone, skype, piece of paper, whisper in the ear). Same paradigm work with messages. Maximum file size is 1GB.
Bit Drop – Offers secure file transfer. It features 256 bit AES Encryption, does not require account creation, file self-destruct after 24 hours, anonymous shared notifications via SMS or e-mail.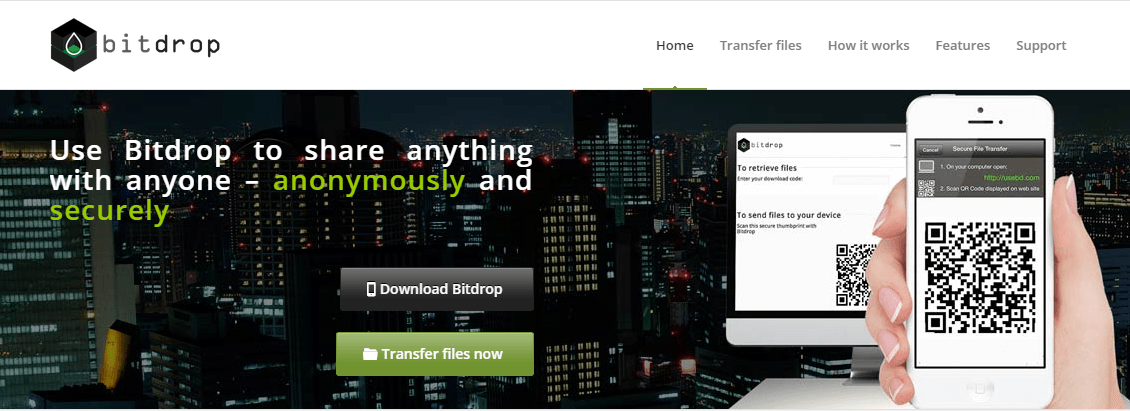
FileTea – Similar to Bit Drop secure file sharing service with a difference that it’s still in BETA.
Encrypted USB Sticks:
This may look like an outdated option for some. USB encryption however is being practiced for longer period of time henceforth there exist more technologies to encrypt/lock the whole file system on the drive rather than just a message or a file. Most of these solutions are also free and available in the form of applications for your operating system requiring a couple of mouse clicks to encrypt your drive. You can easily find lots of options on-line.
There is a great Con that comes with this. You have to prepare the drive and give it to the person yourself instead of just sending an e-mail with an attached file or something. For those who wouldn’t bother doing so there’s another way.
What Are We Left With?
World wide web is a place where magic happens. We find entertainment, news, studies, sometimes even love interests on-line. It is natural that communicating and doing business is no exception. Computers & Internet are great tools for doing that but is it safe to use them?
There’s no general answer to that. Trying to answer it we can say ‘you are safe if your tools are properly configured’ meaning you have to encrypt your data, secure cloud storage, use strong passwords and protect your operating system with antivirus and firewall.


 About the Author:
About the Author:










Wow! This post was really informative mate. Thanks for sharing this. This is the truth “World wide web is a place where magic happens.”
Welcome here and thanks for liking our article. Stay with us to get more like this…