
If you have seen Hollywood horror movie Zombieland, Resident Evil or Dead Snow etc., then you have a rough idea about zombie. Zombie is basically people, who was healthy once and who is infected by virus. According to movies, they can infect any other healthy people or kill them. Scientists create different viruses and zombies for various experiments. However, though zombies are only real in movies, zombie computer is a reality in real life. Check your email now and you will see hundreds of spam email lying in the spam folder. Even you can receive hundreds of spam email every day. So, from where do they come? Do hackers sit down and send hundreds of email manually? Unfortunately, no! All of this work is done mostly by using zombie computers. Hackers do not have only one or two infected computer. According to a research, a hacker can control more than 1.5 million infected computers from a single computer.
In this article we will learn how hackers can control your computer after making it a zombie, why do they do this and how to protect your computer from being attacked. So, let’s get started…
Table of Contents
What Is Zombie Computer?
- Website of spammers
- Spammer
- Spamware
- Infected computers
- Virus
- Mail server
- User
- Web traffic.
I am not telling like the movie that the computer has come back after the death of the computer and infecting the rest of the computers. Rather I want to tell that zombie computer refers to a hijacked computer, which has been attacked by viruses, malware or Trojan and someone else controls it. It can be a single person, who is controlling your computer or your computer may be controlled by a group of hackers. The most terrible thing is that you will not have any little idea about what can be done by your computer.
Many people may think ”Bro I am an ordinary person. What will anyone do by infecting or hacking my computer?” Yes, they may not hack your computer by targeting you but you can automatically be a victim of this attack. This type of attack is not done targeting someone. Infecting your computer means that they have got another soldier into their army.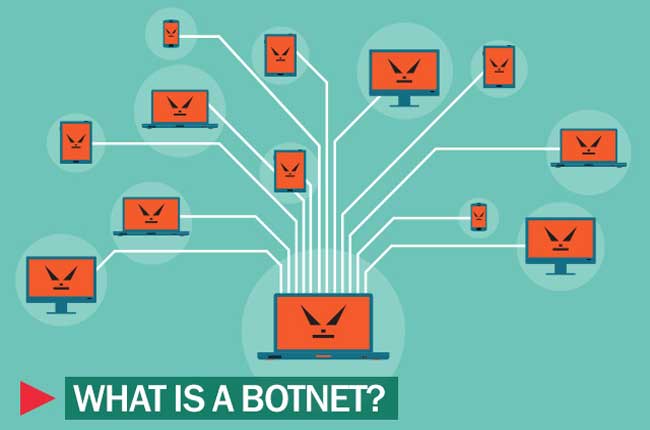
What Is Botnet?
When hackers create a whole army of infected computers, then that is called botnet. Only the botnet commander can issue an order to the zombie computers of that botnet and the entire botnet is controlled via the internet. In this system, it is impossible to trace the computer which operates the botnet. Most computer users may not even know that his/her computer is performing crime for someone else.
Computer Hacking:
You may become surprised to know that most of the computer hacking is done by those peoples, who have no knowledge about computer programming. They use very small program to find errors in your computer’s operating system or any installed software of your computer and try to take control of your computer. These attackers are called cracker. Botnet investigators say that the programs of the hackers are too ordinary and sometimes many people try to hack with the virus of others. Crackers inject these viruses into your PC and turn your computer into a zombie computer.
However, if hackers want to infect your computer, the virus software is needed to be installed in your computer. They plant malware in your computer by sending spam email, through the P2P network or via internet websites. Crackers change the name and extension of the malicious software, so that you may grant it as an important software or file. No matter how much you realize about this attack from internet or from this article and become careful, crackers will find new methods to make you infected.
Many times, a variety of popup message appears while visiting a website or after opening a website, sometimes those messages contain a lot of information about offer and sometimes they ask to subscribe the email. To cancel the popup, every popup has a cross or cancel button. Most of the time we click cancel button. Cracker can hide malware download link in that button and download it technically in your system. The malware file formats are usually known to you, usually image file, .mp4 or .PDF file. Due to the format is known to you, you will open them undoubtedly. A lot of computer anti-virus software catch them after opening the file. The computer survives immediately. If they are not caught, then nothing happens after opening the file. People thinks that there is some problem or the file is corrupted. The malware takes control of the operating system and become associated with the Auto Start program. When you will turn on the computer, the malware will become active immediately. Hacker take control of your computer internet traffic directly via the malware and get the permission to remote access your computer.
Thus, one after another cracker infect hundreds or thousands of computer and build an army or botnet with all the zombie computers.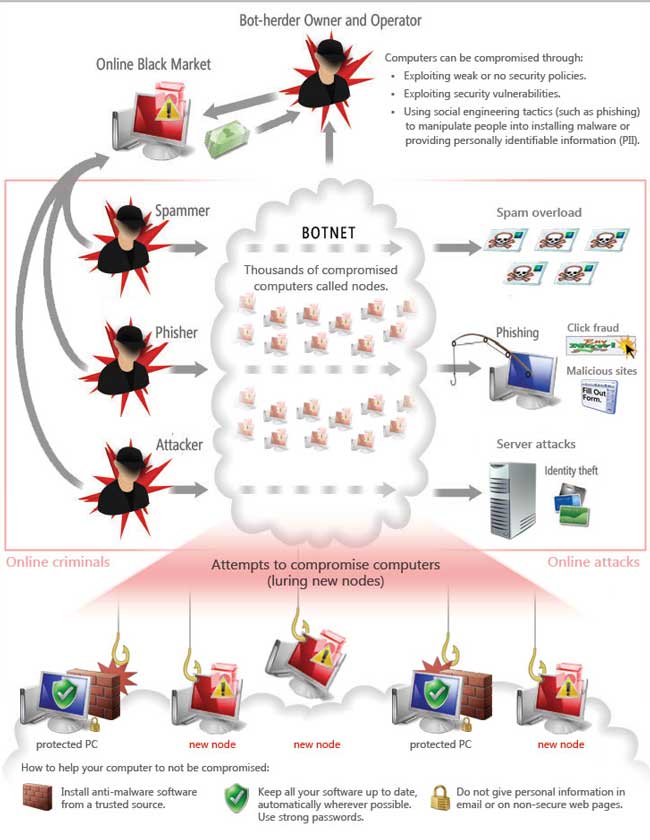
What Does Botnet Do?
Surely now a question has come to your mind ”Well, what does cracker do by infecting so many computers or making botnet? The answer is actually very simple. As the hacker has hijacked your computer cheating you, the original work of the cracker is to cheat many more people for money by utilizing your computer. But the question is ”how are these works done?”
Spam:
Spam is really an annoying thing. Fortunately, the spam filters of your email provider system is much improved now. According to the FBI, most spam emails come from zombie computers. It is relatively easy to trace a spam email, which is sent from a particular computer but the cracker sends spam email using a zombie computer as a proxy and many of them use botnet to send spam email. Tracing them is like finding a needle in the haystack. Millions of spam email can be sent from a botnet at once. Now the question is ”what is spam email?” In fact, this is the weapon by which the cracker spread malware and turn new computers into zombie.
DDoS Attack:
Sometimes, crackers try to make a specific website or web server down by attacking with their botnet. A heavy quantity of fake malicious traffic is sent to the server from millions of devices, which the server cannot control and website becomes down. This type of attack is called DDoS attack. In a variety of ways, crackers can run DDoS attack using their botnet. In some DDoS attack, a heavy number of bot generated fake traffic is sent to the server to crash the server. In some attack, a large amount of email is sent to the server using mail bomb to make the email server down.
Click Fraud:
Sometimes, crackers do click fraud by using their botnet. You may have seen a variety of polls in internet, where people vote on any topic. If crackers want to make any topic winner, then they can do it using their botnet. Suppose you have advertised in a website to promote your business and you pay for every single click, now the website can send fraud click to your advertisement using botnet and earn money from you. There are some websites in online, who sell web traffic. You may have seen advertisement in the internet saying ‘take this much hits to your website for this much money.’ Most of these websites send fake traffic to your website by using botnet.
Is Your Computer A Zombie?
This is not an easy question to answer because viruses and malware are made in such a way so that they don’t get caught. So, even if your computer become zombie, it will be difficult to catch. However, there are some points below. You can check them. If the behavior of your computer match these points, then may be your computer has become a zombie.
- The malware or viruses, which are installed in your system to make your computer a zombie computer, they will use the processor and RAM of your computer system. If you notice that without doing any work, your computer is working slow or 100% disk, memory, CPU is being used, then your computer may be infected.
- Check the sent messages of your email account. If you see sent messages but you never did it, then your computer may have been infected.
- The IP addresses of the zombie computer are kept into the blacklist. First, go to google and type ‘What is my IP?’. Thus, you will find your IP address. Then, you can check from that website, whether the IP is blacklisted. If the IP is blacklisted, then your computer can be infected.
- Since the cracker control your computer via the internet, so keep an eye on your internet bandwidth. If you see that your bandwidth is being consumed in high speed, then may be the cracker is controlling your computer.
How Can You Protect Your Computer From Becoming A Zombie?
You certainly would not want that your computer become a zombie computer. So, you have to protect it from becoming a zombie but how? There is no reason to worry about. I’m going to teach you some of the best steps. Your computer can be the maximum protected by following these.
Antivirus Software Is Necessary:
You must need the best security practices to stay safe and antivirus software is also required with that. You can use good antivirus software like ESET, Quick Heal, Bitdefender etc. by purchasing them. However, never use any version of antivirus software. If you can, then stop the usage of all software because you can be affected through them. If you are using free version of AVG or Avast antivirus software, you must keep them updated on a regular basis and you must try to use paid antivirus software. Beside antivirus, you should install a better spyware scanner. These scanners monitor the internet traffic on your computer and warns you if they find any technical suspect. You must keep anti-spyware program updated.
Use A Firewall:
Install a good firewall to protect your network. There is a default firewall with your router. Please enable the firewall. You also need to update the router firmware straight away. If you are not using a router, then use a good firewall in your computer. Now many antivirus has different firewall.
Strong Password:
Strong password is a must in computer security. Use such a password for any account, which no one can guess easily and do not use the same passwords in multiple places. It’s better to make a long password. Use a good password manager to remember all the passwords.
What Will You Do If You Are Attacked With Zombie Virus?
If your computer is already infected and turned into a zombie computer, then you need to go to a computer specialist. If it is not possible, then scan your system with good quality antivirus and anti-malware. Then the malware, which added relation between your computer and the cracker will be removed. It is not possible to detect the virus, then unfortunately you may need to format your computer’s hard drive and install a new operating system. In this case, do not forget to keep a backup of your data.
Last Word:
Your computer is certainly the most valuable computing device. Unfortunately, it is also valuable to the crackers. I think you can save your computer from becoming a zombie computer, if you follow every topic described in this article. I hope that today’s article will be helpful to every computer user. Do not forget to comment your questions. If I have missed any security tips, I hope you will tell.

 About the Author:
About the Author:






Be the first to write a comment.